Exploited and critical CVEs need to be prioritized as soon as possible to limit exposure.
But manually gathering the full picture needed to make smart prioritization decisions is tedious.
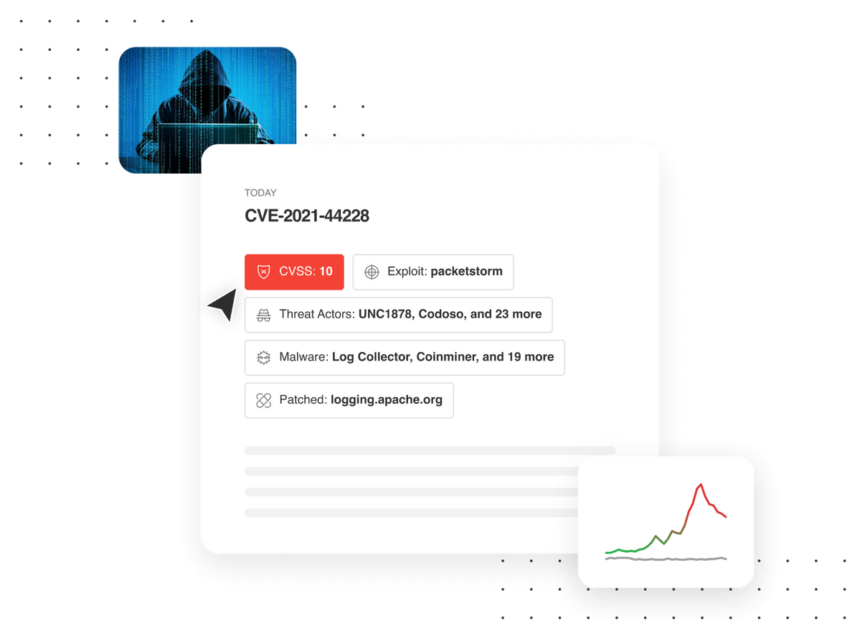
We are excited to announce the new Feedly AI CVE Insights Card.
It’s a machine learning model that aggregates, analyzes, and synthesizes vulnerability information from across the web in real-time so that CTI teams can easily:
- Get a 360-degree view of a CVE without having to open a multitude of tabs
- Discover critical, exploited, and trending vulnerabilities early
- Easily link vulnerabilities to threat actors, malware families, and TTPs
- Predict the CVSS severity, CWE, and popularity of zero-days
Curious how it works? Here is a quick tour
Feedly AI aggregates CVE information from NVD, 25+ vendor advisories, Github, and 10 trusted exploit sources to offer you in one place all the information you need to prioritize an emerging vulnerability.
Feedly AI also predicts the CVSS severity and CWE when it is not yet available on NVD.
You can use the cut-and-paste action to capture the information you need to create a ticket for your team to review this vulnerability.
Feedly AI identifies links between the CVE, threat actors, and malware families by analyzing news articles, threat intelligence reports, and social media posts.
This graph also captures how many sources and social media accounts are mentioning the CVE and compares it to the number of mentions of other CVEs of the same vendor, allowing you to detect trending vulnerabilities early.
Feedly AI organizes all the information he aggregated and analyzed into 3 buckets: vendor advisories, references (trusted and highly curated cybersecurity sources), and social media chatter.
As soon as Feedly AI discovers a mention of a vulnerability on news sites, research blogs, vendor advisories, or social media posts, he will create a CVE Insights Card. You can access the CVE Insights Card of any CVE using the URL format.
Here are some examples of CVE Insights Cards you can explore: CVE-2021-44228, CVE-2022-22965, CVE-2022-1388, and CVE-2022-26134.