Finding and collecting relevant indicators of compromise is critical to your security, but with millions of articles to sort through, discovering and collecting the right ones is a challenge. Even if you know where to look, IoCs can be easy to miss and tedious to upload to your threat intelligence platform.
This is why we’re excited to announce that now you can discover, collect, and export malicious IPs, domains, hashes, and URLs mentioned in your Feeds or across the web, because Feedly AI recognizes indicators of compromise.
We trained Feedly AI to understand, find, and even export IoCs, so that they are easier to find and prioritize. This feature is included with Feedly for Cybersecurity.
Being able to track IoCs with Feedly has been very helpful, our team has been using the new feature every day to be on top of potential risks. Just today, Feedly AI was able to spot three IoCs in a long report I was reading although I hadn’t noticed them.
Collect IoCs from across the entire web
Feedly AI recognizes malicious IPs, domains, hashes, and URLs within the text of articles, Tweets, or Reddit posts, and tags articles so you know how many and what type of IoCs appear in a given article.
When an article contains an IoC, Feedly AI will highlight it for you so it’s easy for you to find and confirm, even if it is buried in the text of a long article or threat intelligence report.
If the IoCs are relevant, you can export them to a markdown or STIX file that will include critical context such as the article link, malware, threat actor, CVE, product, and TTP information.
To track indicators of compromise from across the entire web, click the robot symbol on the left hand navigation menu, and navigate to the ‘Threat Intel” tab. Type “Indicators of Compromise,” then click “+ AND” to refine your AI Feed further if needed.
Now that I can use Feedly to track IoCs across the web, our process to upload new indicators to our environment is much faster and easier. Being able to track IoCs across millions of sources on the web helps us cover every base possible.
Find and export indicators of compromise
Feedly for Cybersecurity is an OSINT platform used by more than 100 cybersecurity teams globally to speed up their threat intelligence. See how Feedly can help you conduct threat research up to 70% faster by starting a free trial.
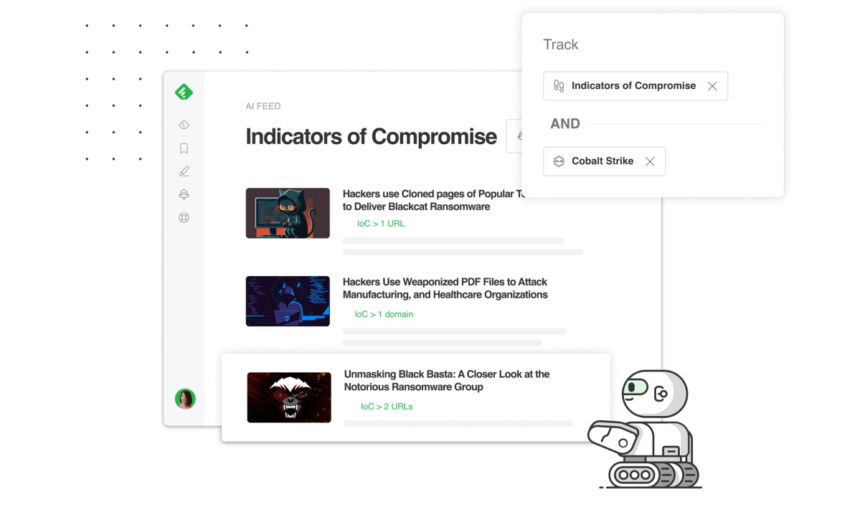
Find IoCs related to a specific threat actor or malware
Let’s say you want to search for indicators of compromise related to a specific threat actor or malware. You can use AI Feeds to flag IoCs that match your query, even if the articles are from sources you don’t specifically follow.
The AI Feed shown in the example below will look for IoCs related to the Cobalt Strike malware family, making it easy to find what’s relevant, export it in seconds, and proactively monitor the web for future IoCs relevant to you.
Find and export IoCs and their context
When you open article(s) that contain IoCs you’d like to upload to your preferred threat intelligence platform, you can export them in either STIX or Markdown formats. This is a significant time saver in contrast to scrolling through the article and copying and pasting what you need.
Your export will also include the IoC context such as the original article link, related malware, threat actor, CVE, product, and TTP information. This makes it even easier to take action. Here is an example of a STIX export:
Automate your IoC collection process with the Feedly API
The Advanced Feedly for Cybersecurity plan includes up to 100,000 requests per month and the full power of the Feedly API. Any action a user is taking in the Feedly application can be performed via the Feedly API, including collecting IoCs. You can access instructions for doing so here.
You can use the Feedly API to aggregate indicators of compromise and their context (associated threat actors, malwares, vulnerabilities and TTPs) from recent articles in a Feed, and return a single STIX object with all of those components and their relationships.
To learn more about the power of the Feedly API or begin a trial or proof of context, click here.
“It used to be particularly tedious to track the IoCs that are related to the critical UI CVEs or products my team has to be on top of. Now, with Feedly’s new IoC feature, I can track IoCs in a much faster and more visible way.”
Find relevant IoCs previously published online
Finally, if you need to search for a specific set of IoCs already published online, you can do this via Power Search. Power Search allows you to leverage Feedly AI’s knowledge graph within your existing Feeds or across the web, allowing you to get much more granular and accurate than standard web searches.
Click the “?” icon in the left navigation menu to access the Power Search screen. From here, you can look for any articles that contain indicators of compromise. This is ideal when you need to track a malware family you haven’t tracked before, and want to quickly find known IoCs that are already available online.
The Indicators of Compromise feature, CVE dashboard, cyber attacks Smart Topic, and several more advanced features are included with Feedly for Cybersecurity. This enterprise package is perfect for cybersecurity teams that need to conduct open-source threat intelligence more efficiently. To learn more about any of these features, or start a free 30-day trial, click the link below.
Find and export indicators of compromise
Feedly for Cybersecurity is an OSINT platform used by more than 100 cybersecurity teams globally to speed up their threat intelligence. See how Feedly can help you conduct threat research up to 70% faster by starting a free trial.