The new Cybersecurity Trending Dashboard
Keeping up with the most critical threats, vulnerabilities, and threat actors can be time consuming and overwhelming.
We have been working with some existing Feedly for Cybersecurity customers to create a trending dashboard that offers an at-a-glance overview of the evolving cybersecurity threat landscape.
The Cybersecurity Dashboard is now available for all Feedly for Cybersecurity customers.
Here’s a quick walkthrough of what you can find on the Cybersecurity Dashboard.
Trending threats
The first component of the Trending Dashboard is a list of the trending threats reported across 1,200 different cybersecurity sources (news sites, blogs, or Twitter accounts).
The Cybersecurity Dashboard allows you to get a quick overview of what are the critical threats that are being reported across all the cybersecurity sites the Feedly community is reading. Think of it like a TechMeme for Cybersecurity.
The model producing this dashboard is focusing on the news published in the last 24 hours.
Behind the scenes, Feedly AI reads all the articles across all the cybersecurity sources and Twitter accounts. Leo dismisses articles that are not about cybersecurity threats, clusters the ones that are reporting the same threat, and ranks them using different “features”.
The initial model we are pushing to beta is a global model. This means that your personal priorities and mute filters are not affecting this model (yet!).
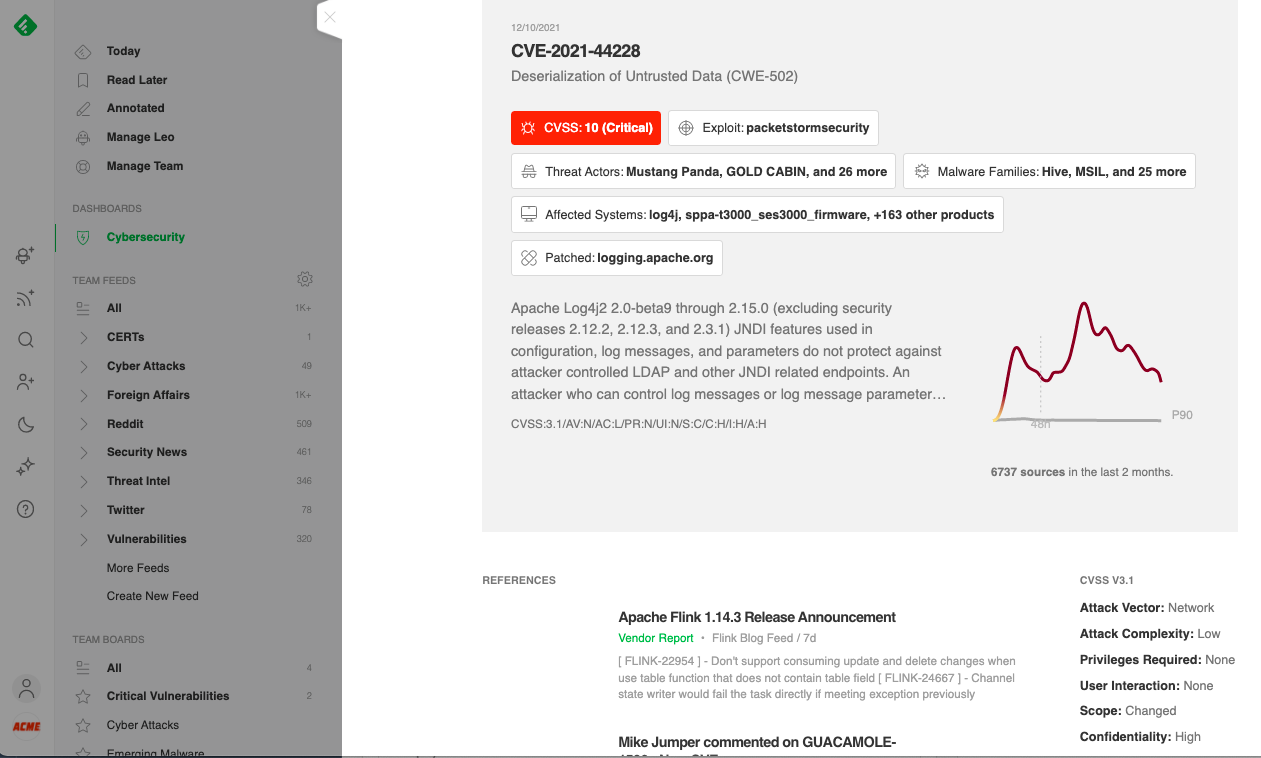
Trending vulnerabilities
The second component of the Cybersecurity Dashboard is a list of the trending vulnerabilities that are being discovered or discussed across cybersecurity sources.
You can click on a specific vulnerability and drill down to a page that captures all the mentions and chatter around that vulnerability.
Trending threat actors
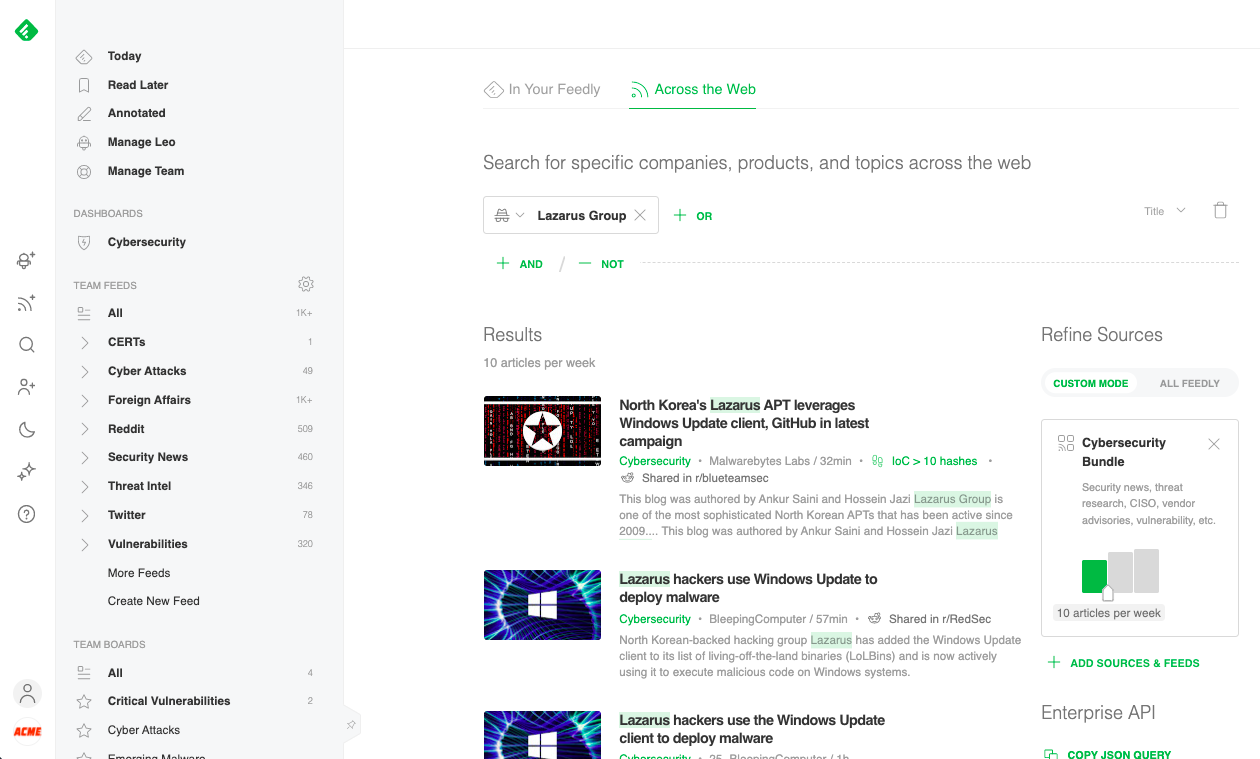
The last component is a list of trending threat actor mentions. It allows you to get an overview of which threat actors are being covered in the news.
You can click on a specific threat actor and get a “Search across the Web” overview of the mentions.
Continuously learning and getting smarter
Every component has a “Less Like This” down arrow button that you can use to provide feedback to Feedly AI. The feedback is going to be reviewed by the product team during the beta to understand how to improve the relevance, deduplication, and prioritization. Feedly AI loves candid feedback.
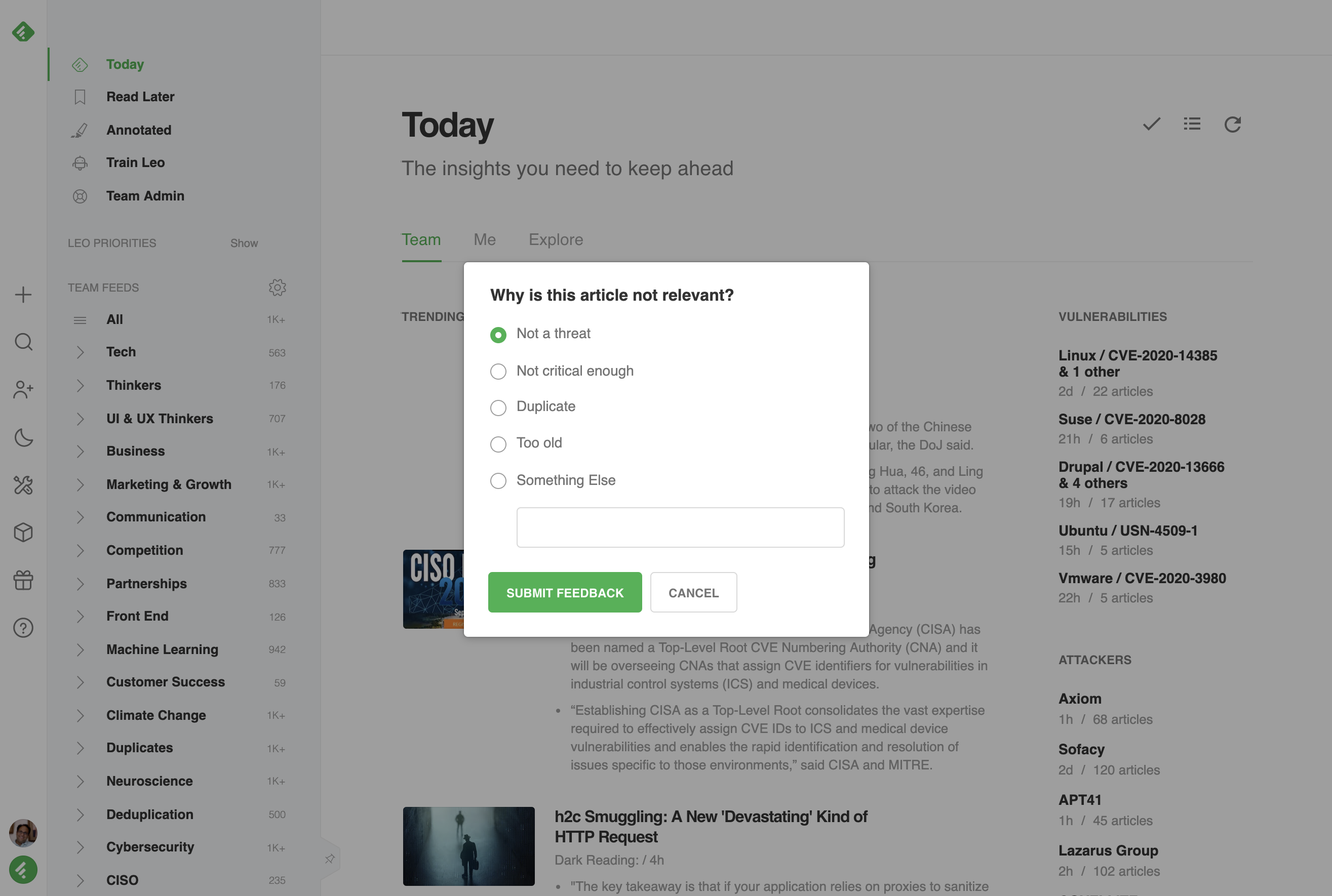
We look forward to listening to your feedback and continuously improving the Cybersecurity Dashboard.
We also want to thank the customers who suggested this feature and worked with us during the Alpha. You know who you are!
Can I personalize the Cybersecurity Dashboard?
Not in the current version. Once we have the core model optimized, we will look at ways to allow you personalize the dashboard by industry, product, threat types.
What is the best way to offer feedback to the product team during the beta?
If you have feedback regarding specific articles or CVEs, please use the’ Less Like This’ button to submit your feedback. If you have ideas on how to improve the AI Model, please email enterprise@feedly.com.
How can I get a demo of Feedly for Cybersecurity?
If you are part of a cybersecurity team and want to get a demo of how Feedly for Cybersecurity can help you streamline your open-source intelligence, you can request a demo and a free trial here.
Can I access the Cybersecurity Trending Dashboard in the Feedly mobile app?
Not yet. The beta is only available in the Feedly Web application. We will integrate this feature into the mobile experience once the beta is complete.





